File Info
| Exam | Certified in Risk and Information Systems Control |
| Number | CRISC |
| File Name | ISACA.CRISC.PrepDumps.2016-03-05.393q.vcex |
| Size | 686 KB |
| Posted | Mar 05, 2016 |
| Download | ISACA.CRISC.PrepDumps.2016-03-05.393q.vcex |
How to open VCEX & EXAM Files?
Files with VCEX & EXAM extensions can be opened by ProfExam Simulator.
Coupon: MASTEREXAM
With discount: 20%
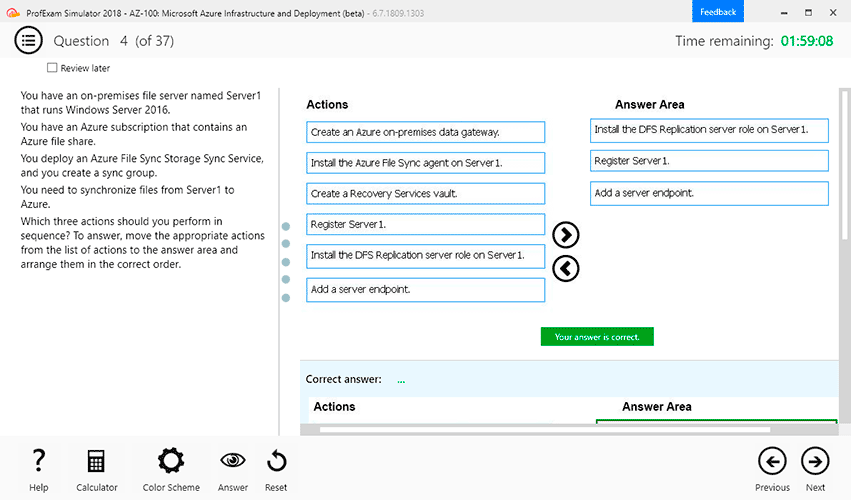
Demo Questions
Question 1
Which of the following is the MOST important reason to maintain key risk indicators (KRIs)?
- In order to avoid risk
- Complex metrics require fine-tuning
- Risk reports need to be timely
- Threats and vulnerabilities change over time
Correct answer: D
Explanation:
Threats and vulnerabilities change over time and KRI maintenance ensures that KRIs continue to effectively capture these changes.The risk environment is highly dynamic as the enterprise's internal and external environments are constantly changing. Therefore, the set of KRIs needs to be changed over time, so that they can capture the changes in threat and vulnerability. Answer: B is incorrect. While most key risk indicator (KRI) metrics need to be optimized in respect to their sensitivity, the most important objective of KRI maintenance is to ensure that KRIs continue to effectively capture the changes in threats and vulnerabilities over time. Hence the most important reason is that because of change of threat and vulnerability overtime.maintenance.reporting, but is not the reason for maintenance of KRIs. Threats and vulnerabilities change over time and KRI maintenance ensures that KRIs continue to effectively capture these changes.
The risk environment is highly dynamic as the enterprise's internal and external environments are constantly changing. Therefore, the set of KRIs needs to be changed over time, so that they can capture the changes in threat and vulnerability. Answer: B is incorrect. While most key risk indicator (KRI) metrics need to be optimized in respect to their sensitivity, the most important objective of KRI maintenance is to ensure that KRIs continue to effectively capture the changes in threats and vulnerabilities over time. Hence the most important reason is that because of change of threat and vulnerability overtime.
maintenance.
reporting, but is not the reason for maintenance of KRIs.
Question 2
You are the project manager of a HGT project that has recently finished the final compilation process. The project customer has signed off on the project completion and you have to do few administrative closure activities. In the project, there were several large risks that could have wrecked the project but you and your project team found some new methods to resolve the risks without affecting the project costs or project completion date. What should you do with the risk responses that you have identified during the project's monitoring and controlling process?
- Include the responses in the project management plan.
- Include the risk responses in the risk management plan.
- Include the risk responses in the organization's lessons learned database.
- Nothing. The risk responses are included in the project's risk register already.
Correct answer: C
Explanation:
The risk responses that do not exist up till then, should be included in the organization's lessons learned database so other project managers can use these responses in their project if relevant.then it may not be shared with project managers working on some other project.plan during the project and they'll be entered into the organization's lessons learned database.project, they should be entered into the organization's lessons learned database. The risk responses that do not exist up till then, should be included in the organization's lessons learned database so other project managers can use these responses in their project if relevant.
then it may not be shared with project managers working on some other project.
plan during the project and they'll be entered into the organization's lessons learned database.
project, they should be entered into the organization's lessons learned database.
Question 3
What are the requirements for creating risk scenarios? Each correct answer represents a part of the solution. Choose three.
- Determination of cause and effect
- Determination of the value of business process at risk
- Potential threats and vulnerabilities that could cause loss
- Determination of the value of an asset
Correct answer: BCD
Explanation:
Creating a scenario requires determination of the value of an asset or a business process at risk and the potential threats and vulnerabilities that could cause loss. The risk scenario should be assessed for relevance and realism, and then entered into the risk register if found to be relevant.In practice following steps are involved in risk scenario development:First determine manageable set of scenarios, which include:Frequently occurring scenarios in the industry or product area. Scenarios representing threat sources that are increasing in count or severity level. Scenarios involving legal and regulatory requirements applicable to the business. After determining manageable risk scenarios, perform a validation against the business objectives of the entity.Based on this validation, refine the selected scenarios and then detail them to a level in line with the criticality of the entity.Lower down the number of scenarios to a manageable set. Manageable does not signify a fixed number, but should be in line with the overall importance and criticality of the unit. Risk factors kept in a register so that they can be reevaluated in the next iteration and included for detailed analysis if they have become relevant at that time. Risk factors kept in a register so that they can be reevaluated in the next iteration and included for detailed analysis if they have become relevant at that time. Include an unspecified event in the scenarios, that is, address an incident not covered by other scenarios.the root causes or factors that contribute to positive or negative effects or outcomes. It is used during the process of exposing risk factors. Creating a scenario requires determination of the value of an asset or a business process at risk and the potential threats and vulnerabilities that could cause loss. The risk scenario should be assessed for relevance and realism, and then entered into the risk register if found to be relevant.
In practice following steps are involved in risk scenario development:
First determine manageable set of scenarios, which include:
Frequently occurring scenarios in the industry or product area. Scenarios representing threat sources that are increasing in count or severity level. Scenarios involving legal and regulatory requirements applicable to the business. After determining manageable risk scenarios, perform a validation against the business objectives of the entity.
Based on this validation, refine the selected scenarios and then detail them to a level in line with the criticality of the entity.
Lower down the number of scenarios to a manageable set. Manageable does not signify a fixed number, but should be in line with the overall importance and criticality of the unit. Risk factors kept in a register so that they can be reevaluated in the next iteration and included for detailed analysis if they have become relevant at that time. Risk factors kept in a register so that they can be reevaluated in the next iteration and included for detailed analysis if they have become relevant at that time. Include an unspecified event in the scenarios, that is, address an incident not covered by other scenarios.
the root causes or factors that contribute to positive or negative effects or outcomes. It is used during the process of exposing risk factors.
Question 4
You work as the project manager for Bluewell Inc. Your project has several risks that will affect several stakeholder requirements. Which project management plan will define who will be available to share information on the project risks?
- Resource Management Plan
- Risk Management Plan
- Stakeholder management strategy
- Communications Management Plan
Correct answer: D
Explanation:
The Communications Management Plan defines, in regard to risk management, who will be available to share information on risks and responses throughout the project. The Communications Management Plan aims to define the communication necessities for the project and how the information will be circulated. The Communications Management Plan sets the communication structure for the project. This structure provides guidance for communication throughout the project's life and is updated as communication needs change. The Communication Managements Plan identifies and defines the roles of persons concerned with the project. It includes a matrix known as the communication matrix to map the communication requirements of the project.monitoring. The Communications Management Plan defines, in regard to risk management, who will be available to share information on risks and responses throughout the project. The Communications Management Plan aims to define the communication necessities for the project and how the information will be circulated. The Communications Management Plan sets the communication structure for the project. This structure provides guidance for communication throughout the project's life and is updated as communication needs change. The Communication Managements Plan identifies and defines the roles of persons concerned with the project. It includes a matrix known as the communication matrix to map the communication requirements of the project.
monitoring.
Question 5
Which of the following controls is an example of non-technical controls?
- Access control
- Physical security
- Intrusion detection system
- Encryption
Correct answer: B
Explanation:
Physical security is an example of non-technical control. It comes under the family of operational controls.safeguards that are incorporated into computer hardware, software or firmware, hence they refer to as technical controls. Physical security is an example of non-technical control. It comes under the family of operational controls.
safeguards that are incorporated into computer hardware, software or firmware, hence they refer to as technical controls.
Question 6
You are the project manager of GHT project. Your project team is in the process of identifying project risks on your current project. The team has the option to use all of the following tools and techniques to diagram some of these potential risks EXCEPT for which one?
- Process flowchart
- Ishikawa diagram
- Influence diagram
- Decision tree diagram
Correct answer: D
Explanation:
Decision tree diagrams are used during the Quantitative risk analysis process and not in risk identification.All the these options are diagrammatical techniques used in the Identify risks process. Decision tree diagrams are used during the Quantitative risk analysis process and not in risk identification.
All the these options are diagrammatical techniques used in the Identify risks process.
Question 7
Which of the following BEST describes the utility of a risk?
- The finance incentive behind the risk
- The potential opportunity of the risk
- The mechanics of how a risk works
- The usefulness of the risk to individuals or groups
Correct answer: D
Explanation:
The utility of the risk describes the usefulness of a particular risk to an individual. Moreover, the same risk can be utilized by two individuals in different ways. Financial outcomes are one of the methods for measuring potential value for taking a risk. For example, if the individual's economic wealth increases, the potential utility of the risk will decrease. Answer: C is incorrect. It is not the valid definition. Answer: A is incorrect. Determining financial incentive is one of the method to measure the potential value for taking a risk, but it is not the valid definition for utility of risk. Answer: B is incorrect. It is not the valid definition. The utility of the risk describes the usefulness of a particular risk to an individual. Moreover, the same risk can be utilized by two individuals in different ways. Financial outcomes are one of the methods for measuring potential value for taking a risk. For example, if the individual's economic wealth increases, the potential utility of the risk will decrease. Answer: C is incorrect. It is not the valid definition. Answer: A is incorrect. Determining financial incentive is one of the method to measure the potential value for taking a risk, but it is not the valid definition for utility of risk. Answer: B is incorrect. It is not the valid definition.
Question 8
Which of the following aspect of monitoring tool ensures that the monitoring tool has the ability to keep up with the growth of an enterprise?
- Scalability
- Customizability
- Sustainability
- Impact on performance
Correct answer: A
Explanation:
Monitoring tools have to be able to keep up with the growth of an enterprise and meet anticipated growth in process, complexity or transaction volumes; this is ensured by the scalability criteria of the monitoring tool.technology applications and infrastructure to be effective over time. Answer: B is incorrect. For software to be effective, it must be customizable to the specific needs of an enterprise. Hence customizability ensures that end users can adapt the software. Answer: D is incorrect. The impact on performance has nothing related to the ability of monitoring tool to keep up with the growth of enterprise. Monitoring tools have to be able to keep up with the growth of an enterprise and meet anticipated growth in process, complexity or transaction volumes; this is ensured by the scalability criteria of the monitoring tool.
technology applications and infrastructure to be effective over time. Answer: B is incorrect. For software to be effective, it must be customizable to the specific needs of an enterprise. Hence customizability ensures that end users can adapt the software. Answer: D is incorrect. The impact on performance has nothing related to the ability of monitoring tool to keep up with the growth of enterprise.
Question 9
You are the project manager in your enterprise. You have identified risk that is noticeable failure threatening the success of certain goals of your enterprise. In which of the following levels do this identified risk exists?
- Moderate risk
- High risk
- Extremely high risk
- Low risk
Correct answer: A
Explanation:
Moderate risks are noticeable failure threatening the success of certain goals. Answer: C is incorrect.Extremely high risk are the risks that has large impact on enterprise and are most likely results in failure with severe consequences. Answer: B is incorrect. High risk is the significant failure impacting in certain goals not being met. Moderate risks are noticeable failure threatening the success of certain goals. Answer: C is incorrect.
Extremely high risk are the risks that has large impact on enterprise and are most likely results in failure with severe consequences. Answer: B is incorrect. High risk is the significant failure impacting in certain goals not being met.
Question 10
Courtney is the project manager for her organization. She is working with the project team to complete the qualitative risk analysis for her project. During the analysis Courtney encourages the project team to begin the grouping of identified risks by common causes. What is the primary advantage to group risks by common causes during qualitative risk analysis?
- It helps the project team realize the areas of the project most laden with risks.
- It assist in developing effective risk responses.
- It saves time by collecting the related resources, such as project team members, to analyze the risk events.
- It can lead to the creation of risk categories unique to each project.
Correct answer: B
Explanation:
By grouping the risks by categories the project team can develop effective risk responses. Related risk events often have common causal factors that can be addressed with a single risk response. By grouping the risks by categories the project team can develop effective risk responses. Related risk events often have common causal factors that can be addressed with a single risk response.